Gympie business hit by Cryptolocker virus
One of our clients, a well known and reasonably large Gympie business house was hit by the cryptolocker virus this Thursday morning. The virus payload came in an email supposedly from Australia Post informing the recipient that they had been unable to deliver a parcel and asking them to click on a link to confirm there details. Looked like a genuine email. Inexperience can be a costly thing. Had the user placed their mouse over the link rather than just clicking they may have noticed the address contained ‘.vn.ua’ – definitely not an address related to Australia Post. In addition the text of the email was in fairly broken English. Not what you would expect from an official Australia Post email. As the user said they were just excited to receive a parcel so they clicked on the link without thinking.
Within 5 minutes the virus had begun encrypting files on the affected machine. Within half an hour it had reached out over the network and started encrypting data files on other workstations and the business’ server.
Once the files are encrypted they can not be opened. They are virtually useless. After a period of time the user on the infected machines(s) will be presented with a web page indicating that there files have been encrypted. By going to the link on the page and paying $500 they will give you a decryption key which will let you access your files again. Only problem – it doesn’t work you have just donated $500 to the virus creators.
At this stage the only option is to format the machine, computer or laptop, and reinstall Windows and programs. All encrypted files are lost. If you have used a USB stick in the machine while it is infected, then all the files on that USB stick will most likely be encrypted.. USB network devices can also become infected.
Users of Dropbox, OneDrive and similar cloud storage options need to be acutely aware of the consequences of ransmoware viruses. Should the cloud storage start synchronising the encrypted files from your computer before the infection is discovered it is quite probable that most, if not all, your good stored files will be replaced with encrypted versions which will then be synched down to any other users accessing that same cloud storage.
Hopefully you have a recent external backup that was done prior to the infection enabling recovery of most of your data files to the newly formatted machine. If the backup was done whilst the machine was infected then the backup will most likely also be encrypted and useless.
Cryptolocker Virus – bad news
Breaking news: U.S. authorities have been able to shut down the server from which the CryptoLocker virus/malware is distributed. Unfortunately if you have been infected it is now impossible to get a key to un-encrypt your data.
CryptoLocker is appearing in the local area lately. Similar to CyberLocker virus. Almost impossible to get back encrypted data. Cryptolocker has completley shut down one business in Cooloola in recent times and cost another two days lost work.
This DEVASTATING malware that makes users’ computer files unreadable until they pay a hefty ransom has begun infiltrating Australian computers after wreaking havoc in Britain and the US.
The so-called “ransomware”, known as CryptoLocker, silently encrypts files on Windows computers, along with files on any connected network storage or USB devices, rendering them unreadable. Once the encryption process finishes, it tells users to pay a ransom, which so far has been $100, $300 or two bitcoins, currently worth about $2400.
Offline backups are the only real hope of getting data back.
See this recent article in the Australian for more information.
Removal of CryptoLocker ransomware or CryptoLocker virus as some call it is quite risky and should only be performed by an experienced computer user or computer technician. Simply removing the virus does not decrypt your files. Decrypting or restoring affected files without the key is almost impossible. In the event that major system files have been encrypted it will be necessary to format the hard drive and reinstall Windows and all programs. If the infection has been on the computer for a period of time it can even corrupt the motherboard BIOS rendering your computer useless.
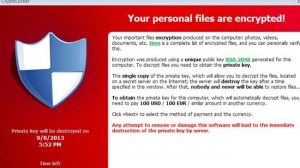
If you are seeing a red screen claiming that all your private documents are encrypted and asking you to pay $300 to decrypt them, the computer is infected with a Ransomware called CyberLocker.
Cyberlocker virus is a member of the family known as ransomware. Once the infection is established on your computer it pops up a message indicating that your computer has been locked and the system and data files have been encrypted. To unlock the files you must pay them $300 to get an unlock key, which may not even work.
Cyberlocker actions:
- It will take control of your computer rapidly once it is downloaded.
- It will encrypt all of your files on the compromised PC.
- It will pretend it ia a legitimate warning and then ask for a ransom.
- It can disable your task manager and even pop up in safe mode.
- It can connect to a remote IRC server and forward the data to cyber criminals without a computer user’s awareness.
- It can’t be simply uninstalled or removed in control panel.
There are many ways your computer could have become infected with cyberlocker ransomware. By far, the most common cause of infection is through the use of browser exploits. The scary part about this is that your PC can become infected by doing nothing more than visiting a compromised website.
In addition to browser exploits, many users become infected from deceptive banner and pop-up ads that disguise themselves as Windows updates or notifications. Once you download their software, which appears innocent, a trojan is installed, allowing the makers to install other software onto your PC.
Cyber Locker and other type or ransom virus these days are utilizing RSA encryption method that is hard coded. It only means that most victims may end up paying for the key if their desire is to retrieve all files immediately. When Cyber Locker enters the PC, it gathers information such as computer name, software versions, and system configuration. Remote server uses these data and assign a unique public key into it, which is just part needed for the decryption process. Another vital section is the private keys that can only be obtain by user upon payment to Cyber Locker.
Regular backups to external hard drives will allow you to restore encrypted documents once the viorus is removed.
For further information on scams, viruses and cons go to the scams page.